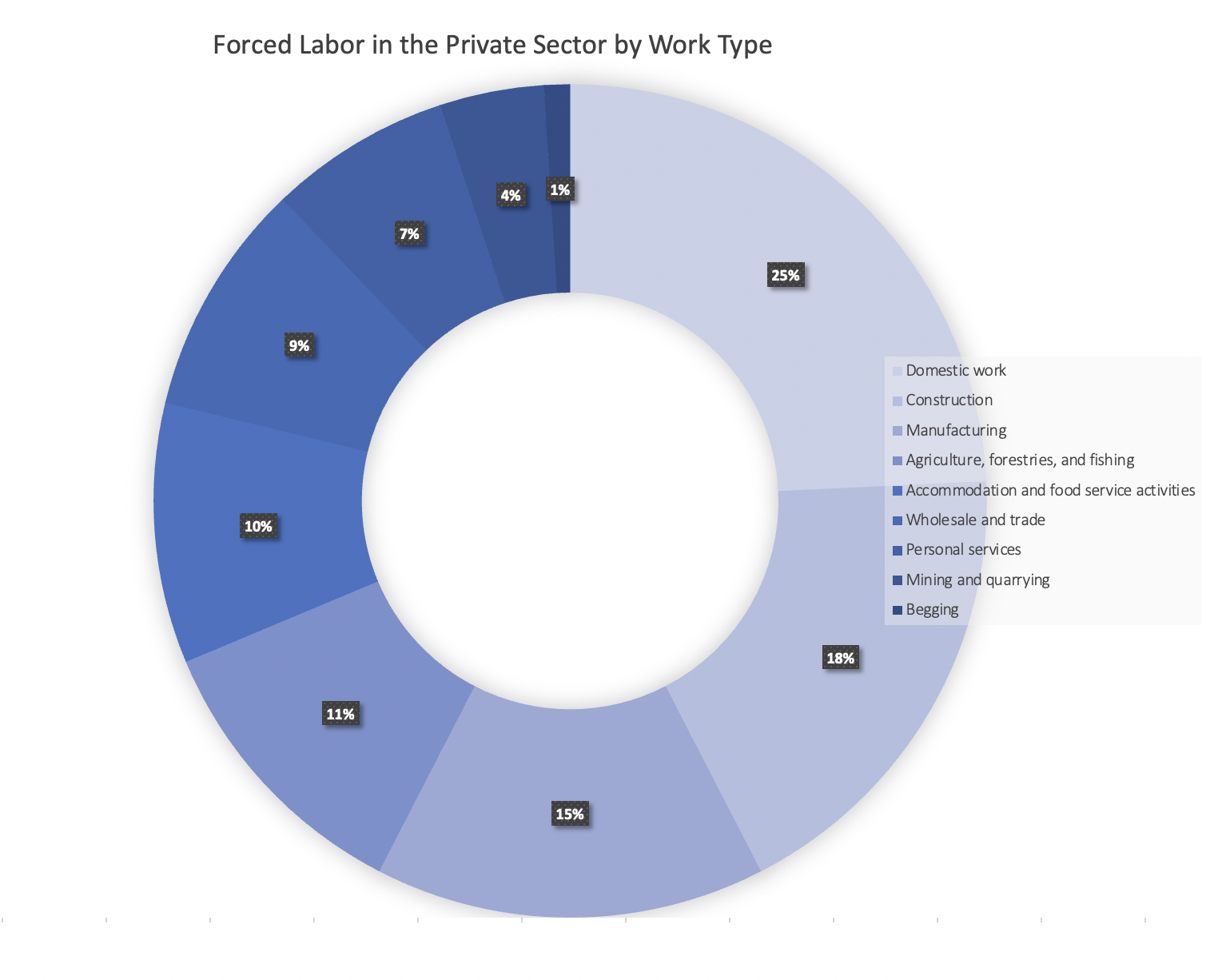
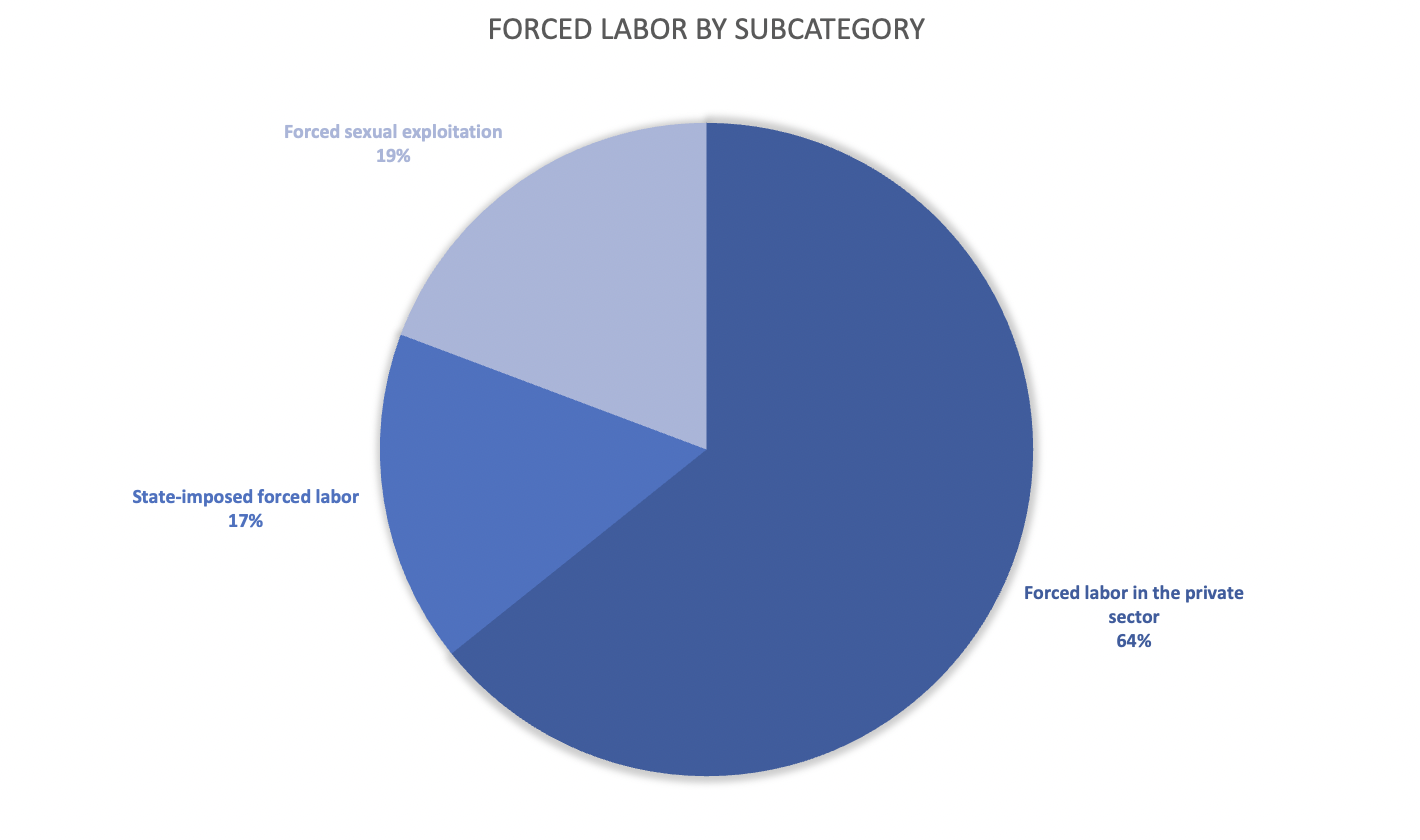
Corporate due diligence is a critical process for managing risks and ensuring regulatory compliance in business transactions. Thorough due diligence helps organizations identify potential risks, verify business information, and...

How to Implement Automated KYC Verification for Your Business
In today’s fast-paced digital world, navigating the complex regulatory landscape can be a challenge for financial institutions and businesses. One critical aspect of compliance is Know Your Customer (KYC) verification. Manual KYC processes can be time-consuming, prone to errors, and inefficient. Thankfully, automated KYC verification offers a streamlined approach, enhancing accuracy and improving the overall customer experience. Let’s walk through the steps to effectively implement automated KYC verification for your business.
Understanding the Importance of KYC Verification
Before diving into automation, it’s crucial to understand why KYC verification matters:
- Regulatory Compliance: Ensures adherence to AML (Anti-Money Laundering) and CTF (Counter-Terrorism Financing) regulations.
- Fraud Prevention: Helps prevent identity theft and financial fraud.
- Customer Trust: Boosts customer confidence by ensuring secure and reliable verification processes.
Assess Your Current KYC Process
Evaluate your current KYC process to identify pain points:
- How long does it take to verify a customer’s identity?
- What’s the error rate in manual verifications?
- Are customers satisfied with the current process?
Choose the Right KYC Software Solution
Selecting the right software is key to successful automation. Look for solutions that offer:
- Comprehensive Identity Verification: Features like document verification, biometric authentication, and facial recognition.
- Real-Time Monitoring: Continuous monitoring and instant alerts for any suspicious activities.
- Data Security: Secure data storage compliant with data protection regulations.
- Customization: The ability to tailor the solution to meet specific regulatory and business needs.
Integrate KYC Software with Your Existing Systems
Ensure the new KYC software integrates seamlessly with your existing systems:
- API Integration: Connect the KYC software with your CRM, banking systems, or other relevant platforms.
- Data Migration: Securely transfer existing customer data to the new system.
- Testing: Conduct thorough tests to ensure everything works smoothly.
Automate Identity Verification Processes
With the software in place, focus on automating core KYC processes:
- Document Verification: Use OCR (Optical Character Recognition) technology to automatically scan and verify identity documents.
- Biometric Authentication: Implement biometric verification, such as fingerprint or facial recognition, to enhance security.
- Liveness Detection: Ensure the system can distinguish between a live person and a photo or video spoof.
Implement Real-Time Monitoring and Alerts
Real-time monitoring is essential for managing risks effectively. Set up your system to:
- Monitor Transactions: Keep an eye on customer transactions for any suspicious activities.
- Generate Alerts: Automatically flag any anomalies or potential risks.
- Automate Reporting: Create automated reports for regulatory compliance and internal audits.
Train Your Team
Ensure your team is comfortable with the new system through comprehensive training:
- System Features: Familiarize everyone with the software’s features and functionalities.
- Best Practices: Educate staff on the best ways to use the system efficiently.
- Troubleshooting: Provide guidance on resolving common issues.
Monitor and Optimize the System
Continuously monitor the system’s performance and make necessary adjustments:
- Performance Metrics: Track KPIs such as verification time, error rates, and customer satisfaction.
- Feedback Loop: Collect feedback from users and customers to identify areas for improvement.
- Regular Updates: Keep the system updated with the latest security patches and compliance requirements.
Best Practices for Automated KYC Verification
- Prioritize Data Security: Ensure robust data encryption and compliance with regulations like GDPR and CCPA.
- Maintain Transparency: Keep customers informed about how their data is used and secured.
- Regular Audits: Conduct regular audits to ensure the system’s integrity and compliance.
- Customer Support: Provide excellent customer support to assist with any issues during the verification process.
Automating KYC verification can streamline your compliance processes and enhance customer trust. By understanding your current process, choosing the right software, integrating it seamlessly, and continuously monitoring and optimizing, you can create an efficient and secure KYC verification system. At iComply, we are committed to making compliance easier, more efficient, and more secure. Our platform offers seamless integration, advanced security features, and customizable tools tailored to your specific needs.
Interested in transforming your KYC processes? Explore iComply’s automated KYC verification solutions today. We’re here to help you navigate the complexities of compliance with confidence and ease. Contact us now to learn more and schedule a demo. Embrace the future of compliance with iComply and keep your business ahead in the competitive financial landscape.