The Only KYC Software You’ll Ever Need
Streamline customer due diligence (CDD) and enhanced due diligence (EDD) with our automated identity verification tools
KYC Verification
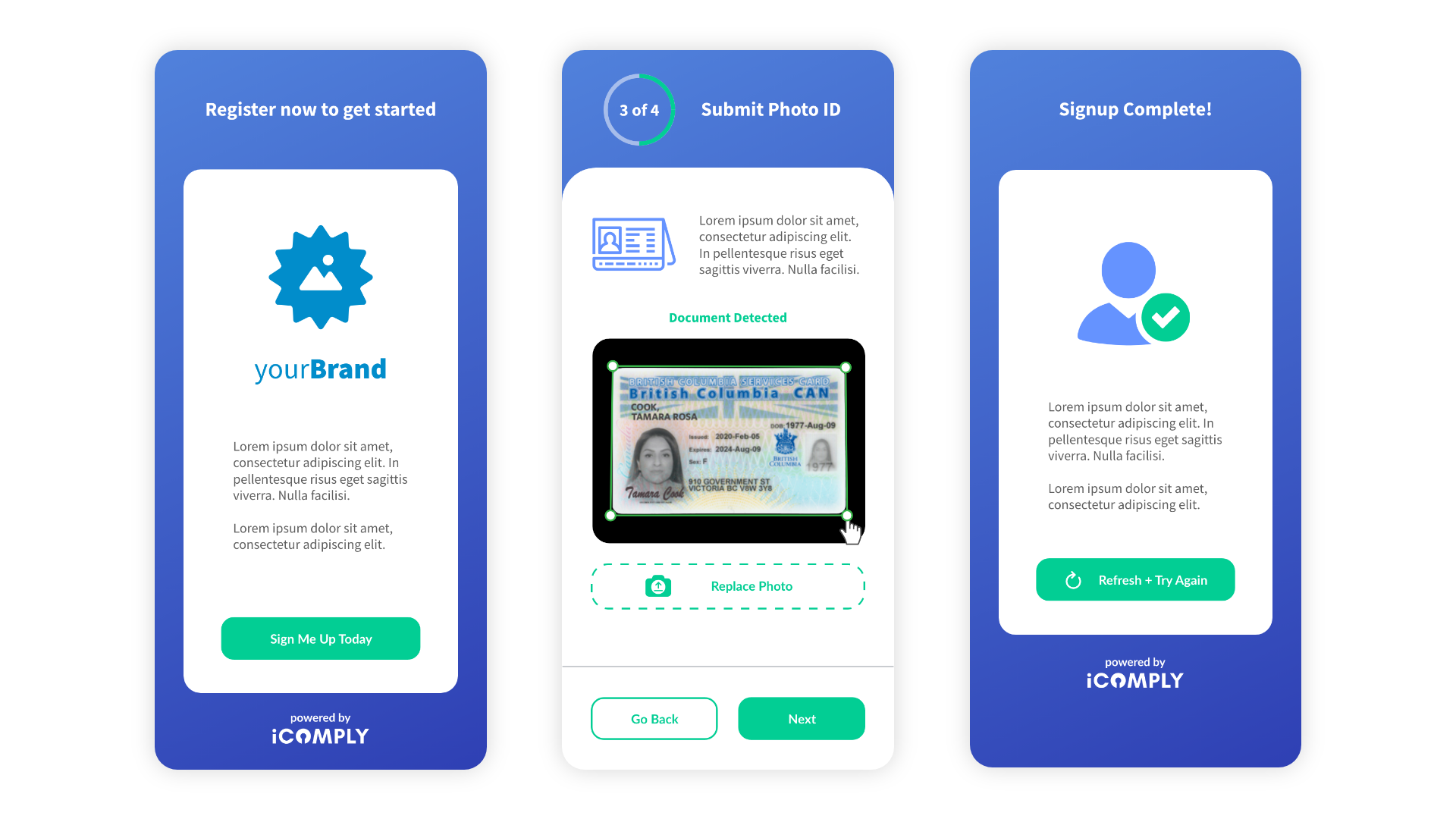
Authenticate over 14,000 driver’s licenses, passports, and identity cards across 195 countries worldwide.
Conduct a liveness test to ensure a person is at the other end of this interaction and face-match to the ID submitted.
Validate uniquely identifiable identity attributes from public records and qualified third parties with the appropriate licenses.

Robust Customization
Add your logo and update the styling so your customers know they’re doing business with you, not some unknown third party.
Configure your onboarding flow to only ask for the information you need with toggles to show, hide, or require fields or modules.
Collect custom requirements from supporting documents or questionnaires unique to your specific industry or procedures.
Start your free trial of iComply
Cancel Anytime. No Questions Asked.
Ongoing Care
Onboarding is only one piece of the AML compliance puzzle, all customers will need some level of periodic account maintenance.
Complete lifecycle management includes comments, scheduled reviews, reports, client updates, and more.
With automated KYC verifications, you can cut processes down to just a few minutes per client for continuous AML compliance.

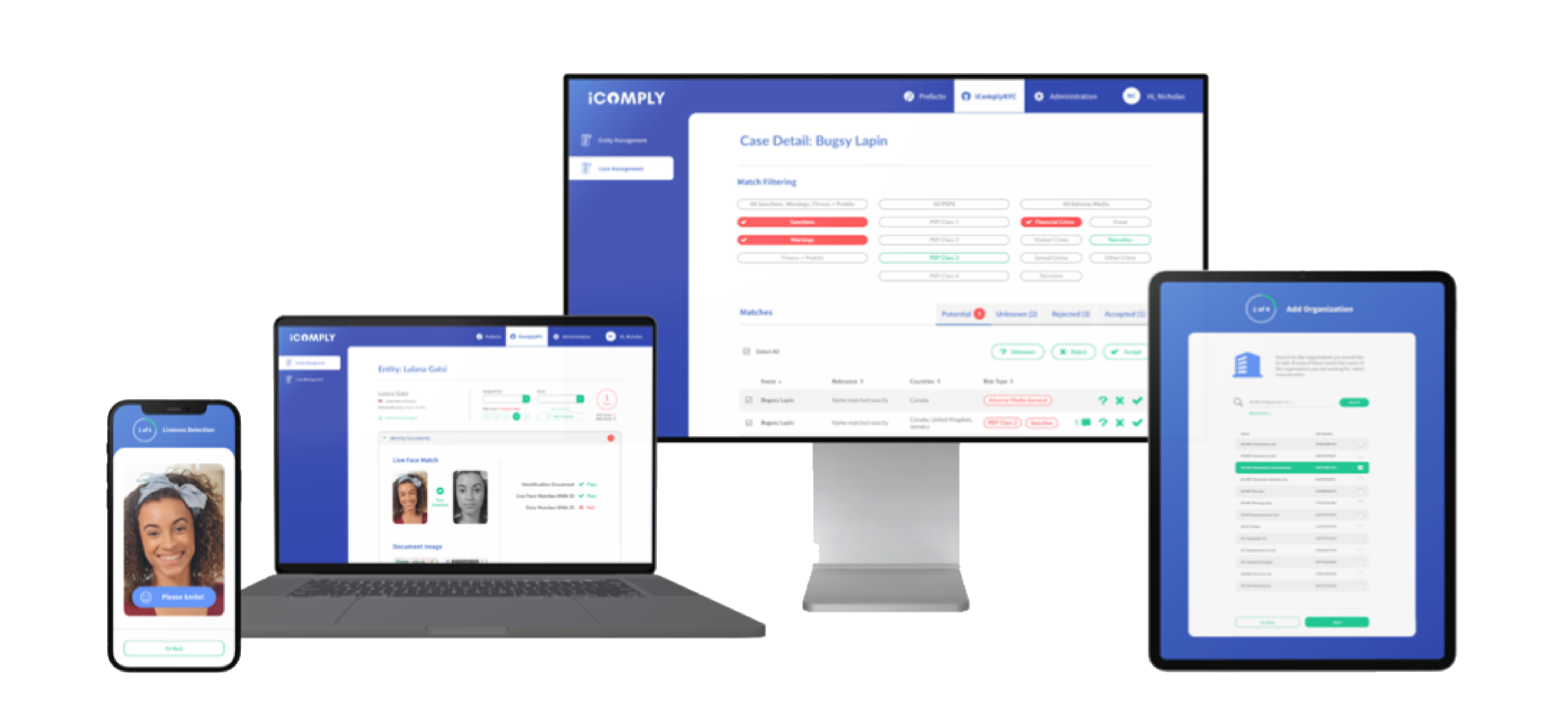
Seamless Integration
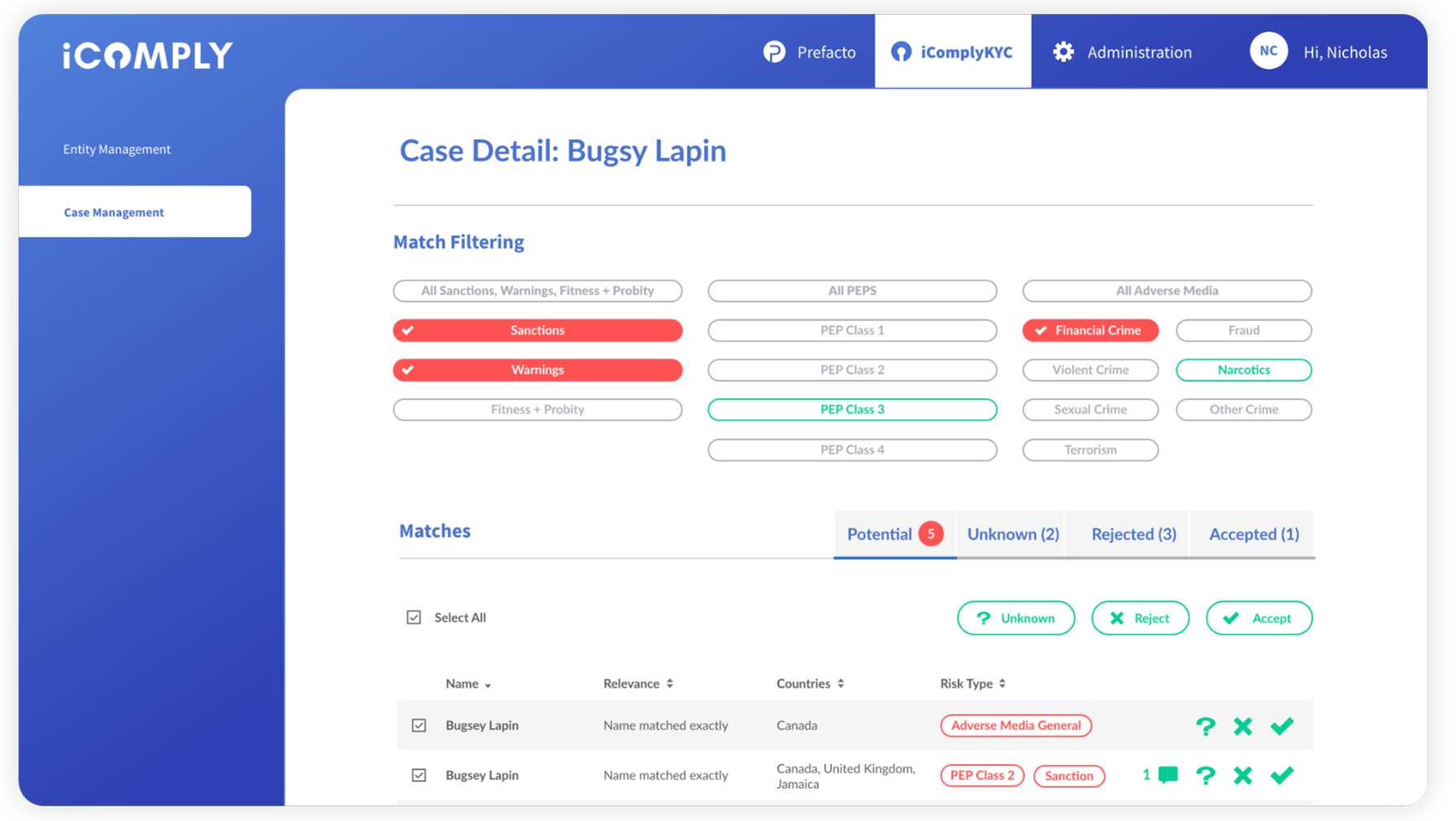
Your automated KYC verifications wouldn’t be complete without daily ongoing monitoring for sanctions screening, politically exposed person screening, and adverse media screening.
Customize your AML compliance risk screening profiles, scoring rules, and levels to access potential risk at a glance.
Auto-assign cases and conveniently investigate source links at the entity or match level to confidently disposition with accuracy.

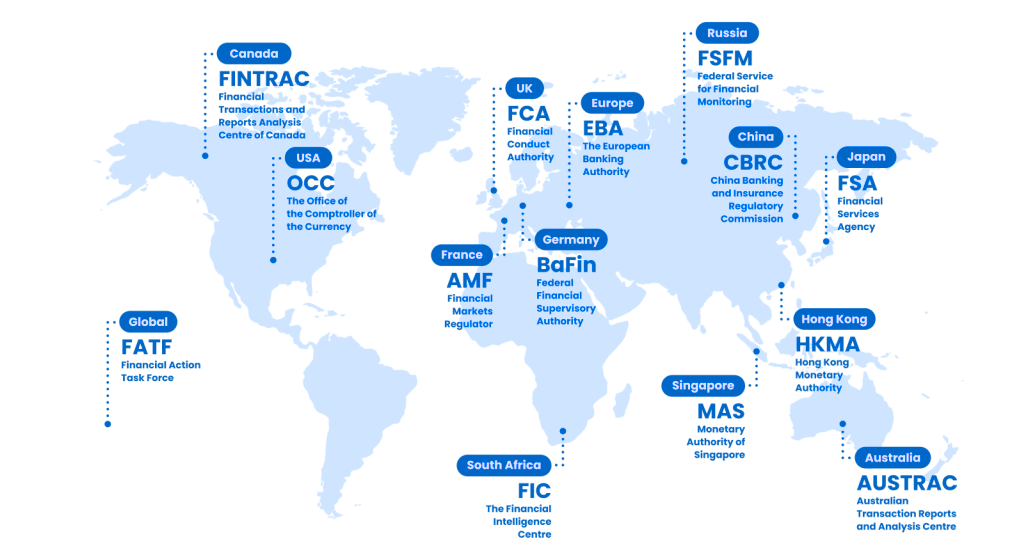
Your Customers Are Global, Your AML Compliance Coverage Should Be Too