Trusted by AML Compliance Leaders Worldwide

Start your free trial of iComply
Cancel Anytime. No Questions Asked.

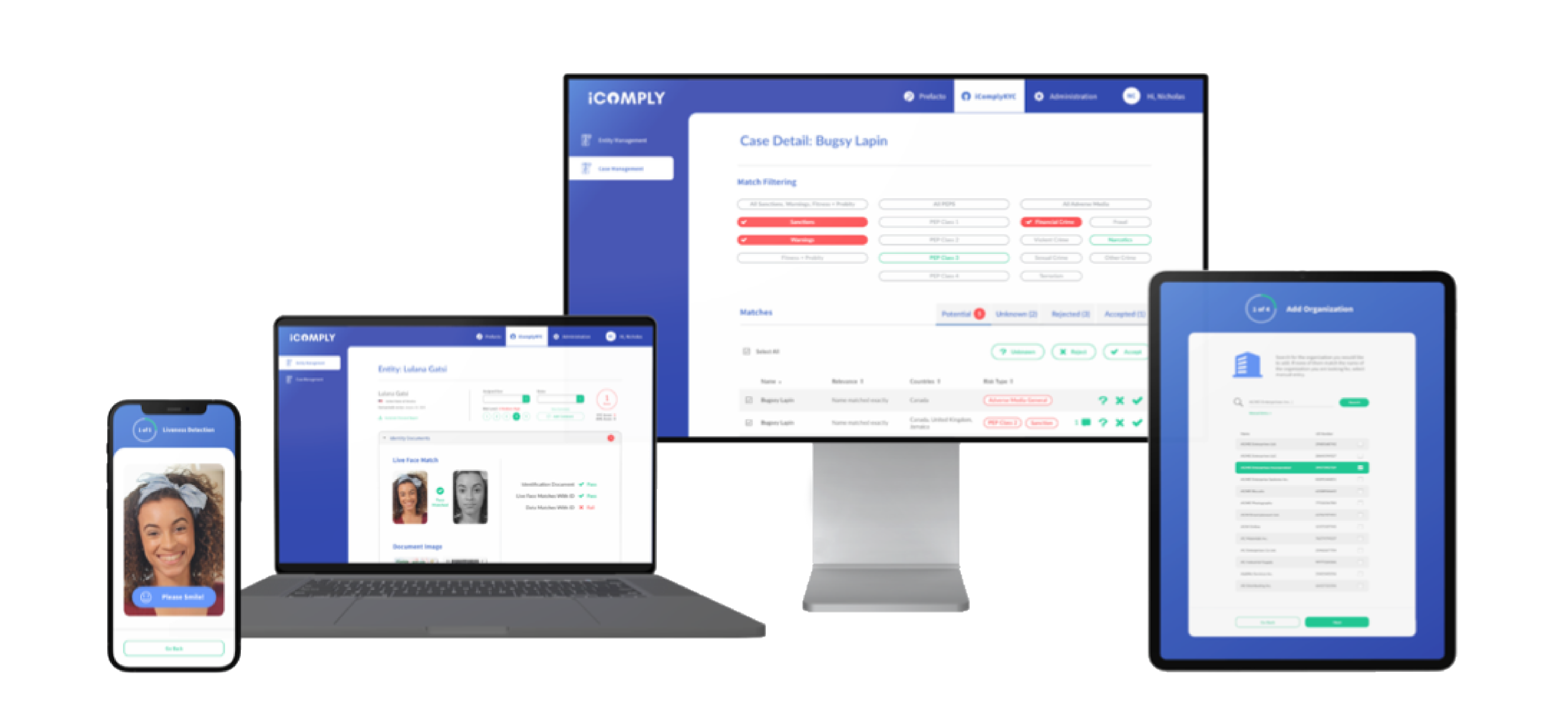
Go Live In Minutes
Choose the right deployment option that fits your unique requirements.
-
Instant SaaS onboarding — Get started in minutes with our no-code console and white-label KYC and KYB solutions.
-
Embedded applications — Integrate with your workflows into any web or mobile app using our plug-and-play SDKs.
-
Custom integrations — Use our secure and encrypted APIs to tailor onboarding, monitoring, and verification flows.
-
Enterprise deployments — Launch iComply in a private cloud or on-premise environment with custom controls.
The Status Quo in AML Compliance is Broken
Here’s how iComply is changing the game
Top 5 Pain Points in AML Compliance
Disconnected tools and vendors – complicates operations and drains development resources, introducing risk, complexity, and uncertainty.
Manual onboarding, refresh, and reviews – time-consuming, error-prone, and impossible to scale across a global customer base.
High false positive rates – overwhelms analysts with noise, reduces trust in your team and your tools, delays time-sensitive investigations.
Limited jursdictional coverage – creates gaps in your compliance, increases regulatory risk, slows market entry, and forces workaround processes.
Offshore data processing and storage – creates cybersecurity vulnerabilities, increase compliance exposure, and fails modern standards for data privacy and security.
How iComply Creates Value
One modular platform for AML compliance – consolidates dozens of vendors into turn-key KYB, KYC, and KYT modules to simplify and streamline compliance operations.
Automated onboarding, refresh, and reviews – saves times, enforces your policies and procedures at scale to ensure accuracy and improve customer experience.
Better signals, less noise – multiple layers of artificial intelligence and robotic process automation flag real risk faster and surface the right signals to your analysts.
True global coverage – supporting unique configurations for up to 195 countries, over 14,000 photo IDs, 142 national languages, and billions of entity and risk data points.
Edge-computing for local processing and storage – protects user data by processing sensitive data on their device and directly transmitting to your preferred data centre.
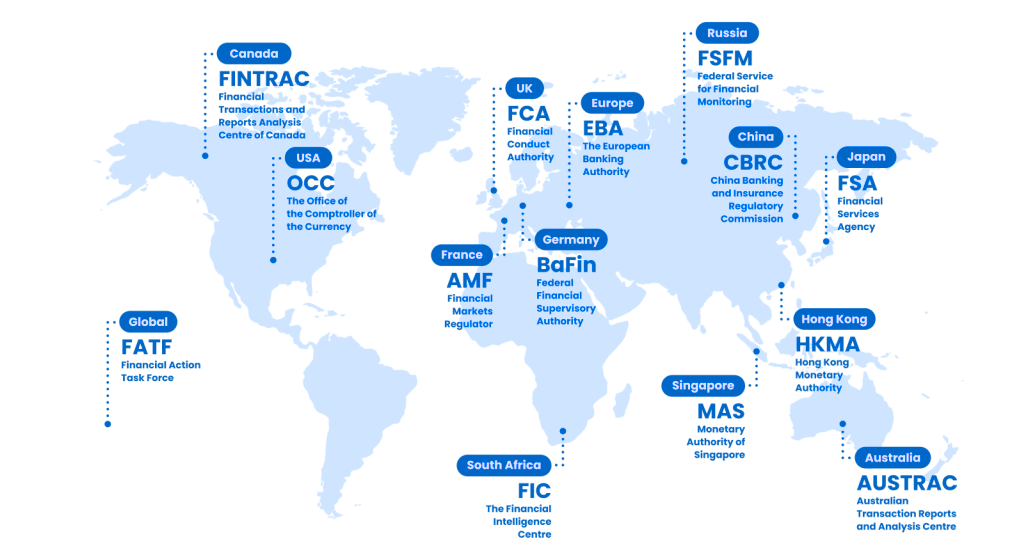
Your Customers Are Global, Your Compliance Should Be Too
Streamline and automate compliance in 195 countries.
14,000+ Identity Documents Templates
3,000+ Sanctions and Watchlists for Risk Screening
11,000+ Trusted Sources for Adverse Media Checks
200+ Million Corporate & Legal Entity Profiles
142 Officially Recognized National Languages
SaaS, Private Cloud, or On-Premise Deployment

What Our Customers Are Saying
“We have settled in with your service and are very impressed. I have every confidence in iComply for the UK, where increasing pressure from regulators to not only improve AML compliance, but also to be able to demonstrate it.”
Start your free trial of iComply
Cancel Anytime. No Questions Asked.

Solutions Tailored to Your Industry
iComply’s flexible KYB, KYC, KYT, and AML compliance solutions easily adapt to the unique industry requirements of:
-
Money Services Businesses (MSBs & MTLs)
-
Legal & Accounting Firms
-
Commercial Banking & Insurance FIs
-
Financial Services Providers (FSPs)
- Fintech, Wealthtech, & Proptech
- Virtual Asset Service Providers (VASPs)


World-Class Privacy, Security, & Encryption
Adhere to local data privacy and protection regulations, standards, and best practices including SOC2 and ISO 27001, CCPA, GDPR, PPIA, PIPEDA, PCI, and more.
Securely process and encrypt all data, including sensitive documents and biometrics on the user’s own device, not our servers, using the power of iComply’s proprietary edge computing.
Leverage cybersecurity best practices and military-grade, end-to-end encryption (TLS1.2, SSL, AES256) to store user data on your preferral servers, clouds, or on-premise locations.

Simple, Transparent Pricing
Whether you’re a startup or an enterprise, we have a plan to fit your needs:
-
-
Essentials – Core functionality for early-stage teams with onboarding, verification, and refresh workflows.
-
Plus – Enhanced automation, more volume, and global flexibility for 195 countries.
-
Pro – Advanced features including KYT transaction monitoring, and volume based pricing tiers.
-
Enterprise – Tailored deployments to your preferred data centre, dedicated success managers, and enterprise SLAs.
-

Have Questions?
Find answers to common questions about setup, features, and compliance capabilities.
Start your free trial of iComply
Cancel Anytime. No Questions Asked.